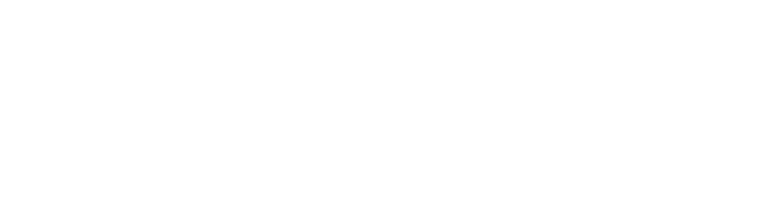Why Your Clients Should Look at Reviewing Their Security/Cybersecurity
Why security is important. How reliant is an organization on information and data? Customer bases. Order processing. Employee files. Proprietary systems/data. Day-to-day functioning. Organizations of every size, scope, industry, and endeavor rely on their data integrity and ability to work with it — from managing a bank’s payroll to protecting a school’s student information to life-critical patient information. Every day you read about organizations being breached in the news. Threats are becoming more sophisticated and frequent. The solutions range from small, easy to embrace ideas, like providing employee training, to extremely complex concepts, like systems that learn to screen for files that behave in certain ways. There’s no “fix in a box”. Cybersecurity requires an overarching plan, dedication, and frequent revisiting.
53% of connected medical devices and other healthcare IoT devices have at least one unaddressed critical vulnerability.
— HIPAA Journal
NIST Framework: Identify, Protect, Detect, Respond, and Recover defined by the National Institute of Standards and Technology agency, provides a good overview of the approach all organizations should take.
Defining the attack threat surface is a fancy way of saying identify the places where you’re vulnerable. To reduce your risk, you reduce the threat surface. Some security experts emphasize an approach of global protection, while others segment the attack surface to minimize the impact of an eventual attack, and avoid organization-wide downtime.
Internal Threats. Some studies find that as many as 90% of threats come from within an organization, mostly from human error or carelessness, but also from malicious employees intending to disrupt operations or steal information. Organizations are encouraged to train their employees to be aware of everything from identifying potential incursions through emails/texts to controlling the devices that attach to the network and sites employees visit on the internet.
External Threats come from all over the world, exploits are even bought and sold on the dark web. Attacks can be targeted, or generalized in nature. They can be extremely aggressive and disruptive or be more subtle, scraping information over time. An attack can stop your organization in its tracks locking you out of important data, compromising infrastructure, or can lead to sensitive/proprietary information being lost or leveraged for illegal capital gain.
5 Common Types of Attacks
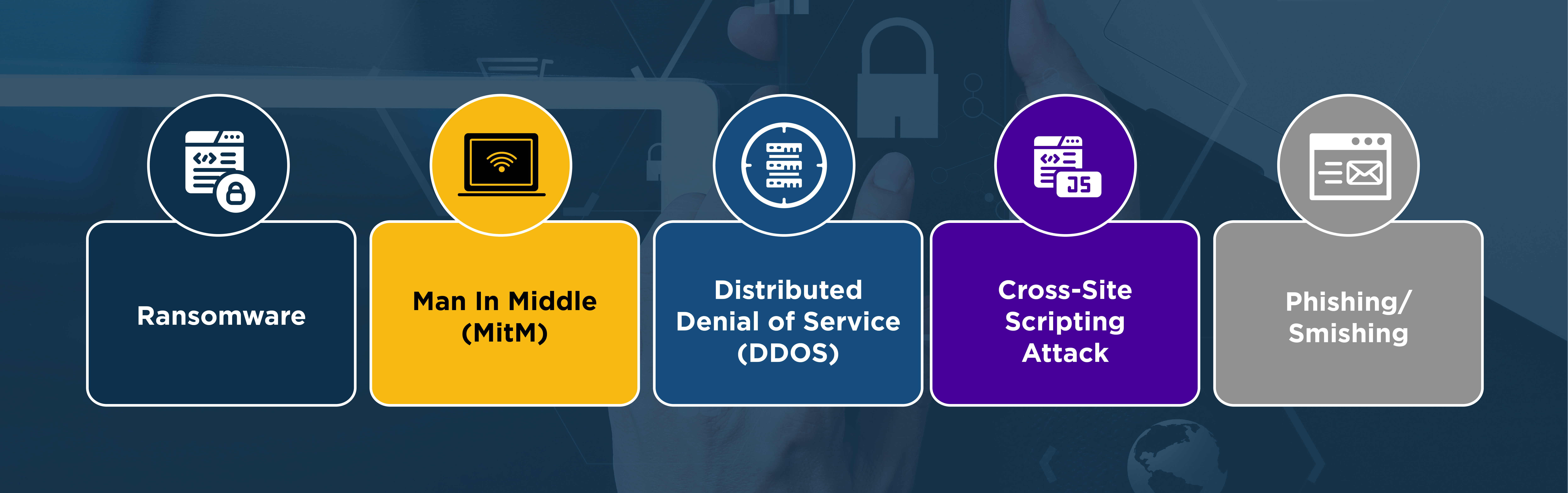
Ransomware. System files are encrypted with a costly payment request to allow the attack to regain access to their files.
Man in the Middle (MitM). Information is caught while being transmitted on the Internet, the hackers will attempt to “sniff” and study the information to see if it can help them breach the system.
Distributed Denial of Service (DDOS). Occurs when more requests are sent to a target server than it can handle, effectively crashing it so it’s unusable. These attacks can be coordinated and last for an extended period of time.
Cross-Site Scripting Attack. This occurs when JavaScript is used to exploit a web application, these attacks can be quite severe and provide a great deal of information to the hacker.
Phishing/Smishing. These attacks fall under the category of social engineering, a hacker sends a webpage URL that looks the same as the legitimate website, tricking the user into submitting their credentials which the hacker can use to gain access to the system.
Known Vulnerabilities, Testing for Weaknesses, and Behavior Profiling. When vulnerabilities and exploits are found, solution providers, including antivirus developers, will provide patches, profiles, and updates to address them. This relies on identifying a problem, finding a solution, and updating it — which can take some time. Alternatively, there are professionals (and some amateur enthusiasts) who will probe to find problems and notify the organizations or developer affected. One of the newer ways that relies heavily on Artificial Intelligence/Machine Learning is to look at known threatening behaviors and flag new interactions that follow these same behaviors.
Invest in Results, Mitigate Damages. In the security game, they say it’s not if you’ll be hacked/breached, but when. Organizations need to be proactive and security-wise — the cost of being unprepared can be heavy with lost operation time, reputation, and the resources needed to recover. Overworked IT departments often don’t have the knowledge, bandwidth, or ability to develop and oversee effective strategies — which is where our Partners, as industry-leading experts, can make the difference by leveraging the Sandler Partners portfolio of Security providers.
More Than Competitive, Leading Solutions and Terms. With 200+ providers, the strongest agreements in the industry, and technical/sales support, Sandler Partners are able to design solutions to the most exacting requirements, plan for future changes/phased integrations, and do it with incredibly preferential pricing. We’re with you every step of the way, providing the level of support – sales, training, implementation, troubleshooting – that you and your clients require. You take point, we’ve got your back!
Interested in learning more? Watch on demand our, “Big or Small, All of Your Customer’s Data is at Risk” webinar with Gerry Davis, SVP of Sales Engineering, where he spoke with industry leaders on how to talk about, and sell, Security solutions.
If you can’t make it, don’t worry, our team is always here to help you expand your Security business!
Our Featured Providers
Rackspace is a leading end-to-end multicloud solutions expert. They combine expertise with the world’s leading technologies- across applications, data, and security. As a global, multicloud technology services provider, Rackspace delivers innovative capabilities of the cloud to help customers build new revenue streams, increase efficiency, and create incredible experiences. Rackspace has deep expertise on AWS, Microsoft Azure, Google Cloud or GCP, VMware, Kubernetes, Oracle, SAP, Salesforce, and many other industry leading technologies.
WiredIQ works exclusively through the channel and provides a complete suite of managed services delivered in one intelligent appliance, the Brain Box. The Brain Box brings together SD-WAN, Managed IT Services, Security as a Service, and Internet of Things management onto one device, while maintaining PCI 3.0 and HIPAA compliance. Additionally, WiredIQ also offers a full suite of Unified Communications applications, a robust Contact Center offering, broadband, and POTS. All WiredIQ applications can be offered à la carte. The All-in-One Brainbox is a separate application and is agnostic to specific phone systems.
AT&T works with Solution Providers to offer the full range of AT&T’s industry-leading portfolio. Solution Providers can use the power of the AT&T brand to generate business growth and help customers accelerate their digital evolution.
DYOPATH provides managed technology services, network design, and data center solutions nationally with 50+ highly skilled engineering resources and a U.S. based 24/7/365 Network and Security Operating Center. Consulting services include regulatory compliance, security assessments, risk assessments, gap analysis, business process optimization, and high level IT strategy. Managed Services include Virtual Cloud Services, ITILv3-aligned Service Desk (Help Desk), managed network and security, disaster recovery, and hosted Exchange.
Our Partners have access to over 90+ Security Solution Providers, including other Security leaders like Verizon, Corvid Cyberdefense, Masergy, TPx, and Lumen. You can review all your available options by using the Solutions Finder tool located in the Sandler Portal. For help navigating your way through the process, while discovering the best provider(s) solutions available to meet your client’s requirements, simply contact our Sales Engineering Team!