Help Your Customers Identify/Assess Vulnerabilities, Prevent Breaches, and Enact Ongoing Disaster Recovery Plan
Whenever there is a breach in a specific industry, it has a ripple effect. Individual organizations urgently look at their own operations, with a heightened desire to close their vulnerabilities. These conversations translate to any organization, in every vertical, but let’s look specifically to those most impacted by this particular breach, auto dealerships. These businesses rely heavily on many platforms, with CDK commonly being of critical importance for their daily and ongoing operational activities. There’s reason to be concerned. This was a targeted breach, and the criminal community will likely try to leverage this reliance to extend further and access additional systems and networks.

Helping your customers identify and address the vulnerabilities/security flaws within their networks (infrastructure, applications, & systems) before they can be exploited is essential. Knowing beforehand allows them to recover/mitigate the impact of an attack. Avoiding a breach is so important for your customer’s:
- Day to Day Operations: How long could your clients be without their network/data/information? Identifying each function allows the ability to prioritize for revenue and business continuity.
- Customer Data Integrity: The CDK breach has likely exposed consumers’ identity and personal information, which may result in theft and financial fraud, severely damaging trust and the dealer’s reputation.
- Financial System Security: Dealerships rely on intricate financial systems for transactions, contracts, loans, and inventory management.
- Inventory and Operation Safeguards: Inventory tracking and management systems are critical. A compromise could lead to significant financial losses and operational disruptions.
- Regulatory Compliance: The automotive industry faces stringent data protection regulations. Regular Penetration testing can help maintain compliance and avoid costly penalties.
- Reputation Management: In a highly competitive industry, a single security incident can irreparably damage reputation.
Evaluate the Dealer’s Breach Response. CDK issued important directives to implement immediate security measures (reset all passwords and activate Multifactor Authentication – MFA). These starting measures should already be complete, letting you move to the next stage, and suggest looking for additional and missed vulnerabilities that will arise in connection with CDK, associated suppliers/partners within their ecosystem, and any other potential weaknesses. Criminals will attack with the intent to compromise information, disrupt activities, cause damage, and profit by selling information or holding it for ransom. Cyber threats in the automotive sector are constantly evolving. For obvious reasons (financial, customer data, large threat surface) your dealership customers have become a favorite target. Regular Penetration testing can help keep their defenses up-to-date against new attack methodologies, referred to as vectors. Pen testing is essential to constantly and consistently evaluate a Cybersecurity program’s posture.
Test for vulnerabilities regularly (monthly or semi-annually). Plus, review/assess your Cybersecurity posture frequently, even annually, if you haven’t before.
CDK Breach Marketing Campaign, Now in Your Marketing Center! Start the conversation with your customers impacted by the CDK breach – access a targeted, customizable campaign within your Marketing Center. Add your logo and contact information, make any additional changes, and distribute directly from the platform. This campaign includes emails, social posts, and a collateral piece.
Also available is the Security campaign, use alternatively or in combination with the CDK Breach campaign.
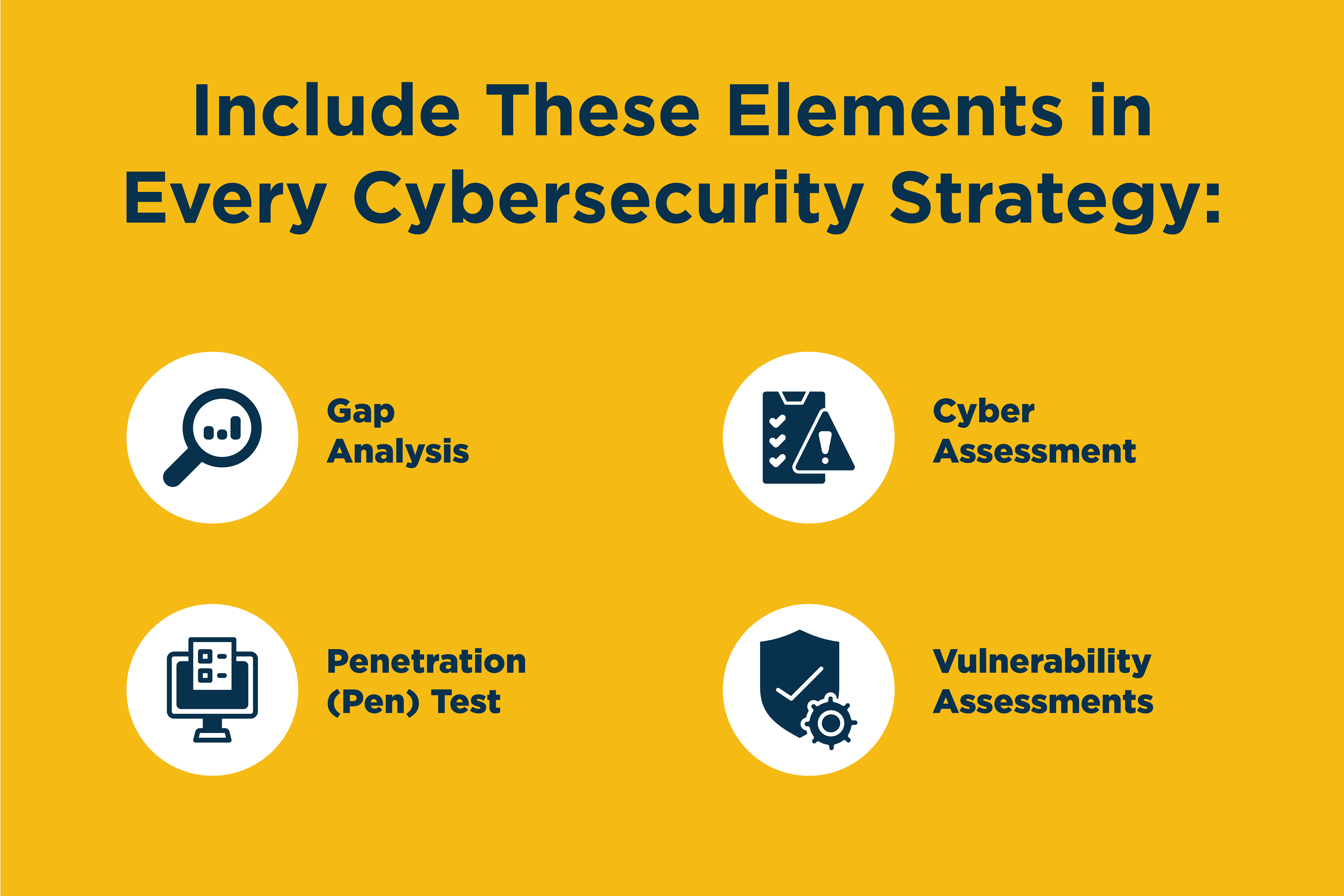
Readiness Requires Action! Many procedures, solutions, and services can help identify just how capable your customer is to stand up to or avoid an attack – easily applied as automated and manual tasks. Help them enact ongoing vigilance with vulnerability scans and timely patch management, actively identifying known threats and implementing the latest security-tested patches to minimize real-world attack threats (identifying potential attack scenarios) and receive reports that empower the ability to prioritize remediation and further patching. These efforts will ensure robust defenses that secure valuable data/systems. These are the same kinds of attacks the cybercriminals use, letting holes be closed before they find them.
Emphasize Planning, Policy, Backup & Disaster Response/Recovery. There is an inevitability to breaches, even a billion-dollar company like CDK Global with all its resources and in-house abilities can be successfully targeted. Being prepared before for what happens after, is how you minimize the impact. Planning and training employees depending on their roles is essential. Reduce/segment the Attack Surface. Write, manage, and maintain policy, which is often a great time to bring in a CISO/CISO consultant; or utilize a Cybersecurity Managed Services Provider (MSSP). Scheduled (onsite/offsite) back-ups/redundancies should be a part of every Disaster Response/Recovery strategy along with a well-thought-out overall plan that is maintained, managed, enforced, and revisited on a regular schedule with support/visibility across the organization, from the C-suite to front line employees.
Cybersecurity is vast, but you’re not alone, you have your Sandler Partner resources to help you – from your dedicated Channel Manager and Sales Engineer (find them listed on your Sandler Portal homepage) to resources in your portal like conversation starters, the Cybersecurity Matrix, pre-built Marketing Center Campaigns, and a tool I use all the time, Solutions Finder, your click-based discovery tool with searchable criteria from every one of our 200+ Providers. CORO, DYOPATH, Lumen, and Cybersafe are great options to review, and be top of mind when you enter into conversations with your customers about Cybersecurity. Your support team can be as heavily invested in the conversation as you want, being a part of the discovery/design stages with your customers or offering a more hands-off approach. The CDK breach is an opportunity to open up the Cybersecurity conversation with your customers, to help their organization, and add to your revenue. Make sure you involve your dedicated Sales Engineer, found in your Sandler Portal dashboard, if you need help engaging your customers in Cybersecurity conversations.
Author:
Eric Beller
Eric Beller, SVP, Sales & Complex Solutions, assists Partners with developing everyday technical solutions in the central region, and complex solutions across the nation. Our resident Cybersecurity expert, we leverage his technical and personal expertise to solve customer’s business problems while also ensuring an elevated experience.